Streamline Your Organization Security Posture with NIST CSF 2.0

Crowdstrike reported a 75% increase in cloud environment intrusions from 2022 to 2023 (source). IBM’s cost of data breach report shows that the global average cost of a data breach in 2024 is USD 4.88M, a 10% increase over last year and the highest total ever. Cyber attacks would scale much faster with the help of artificial intelligence. If organizations are not prepared, the consequences will be dire.
There are many security frameworks that can help organizations enable security and safety for their applications and users. In this blog post, we will discuss NIST CSF, one of the most used security frameworks that helps organizations understand and prevent cybersecurity risks. We will cover the key enhancements in NIST CSF 2.0 briefly, explain the primary components of CSF in detail, and show the best practices for maintaining NIST CSF in the cloud.
What is NIST CSF?
The NIST Cybersecurity Framework is designed to help private sector organizations evaluate and enhance their capacity to prevent, detect, and respond to cyber-attacks. The framework is meant to supplement an organization’s current risk management and cybersecurity procedures.
We can call it an add-on to an organization’s existing information/cyber security posture. The framework offers recommendations based on best practices and industry standards. It assists businesses of all sizes, from startups to major corporations, in determining the best course of action for enhancing cyber-security and cyber resilience and evaluating the present level of their cyber-security processes. In February 2024, NIST introduced NIST CSF v2.0 with several upgrades.
Key enhancements in NIST CSF 2.0
CSF 1.1 has 5 functions, 23 categories, and 108 subcategories. The CSF 2.0 has 6 functions, 22 categories, and 106 subcategories. CSF 2.0 is an extension of CSF 1.1 that includes several category realignments and the addition of the ‘Govern’ function.
Here are key enhancements in NIST CSF 2.0:
- Supply Chain Risk Management (SCRM): NIST CSF 2.0 places a greater emphasis on SCRM. Given the rise of supply chain attacks, organizations are now encouraged to manage risks not only within their systems but also across their entire supply chain.
- Identity Management and Access Control: Enhanced guidelines for managing identities and access controls are included, reflecting the critical role these elements play in securing organizational infrastructure.
- Measurement and Metrics: The updated framework provides improved guidelines on measuring the effectiveness of cybersecurity practices, helping organizations to continuously assess and enhance their security posture.
- Integration with Privacy Framework: NIST CSF 2.0 is more closely aligned with NIST’s Privacy Framework, providing a more holistic approach to managing both security and privacy risks.
- Improved Guidance on Implementation Tiers: The framework offers clearer guidance on the implementation tiers, helping organizations to better assess their current cybersecurity posture and set realistic improvement goals.
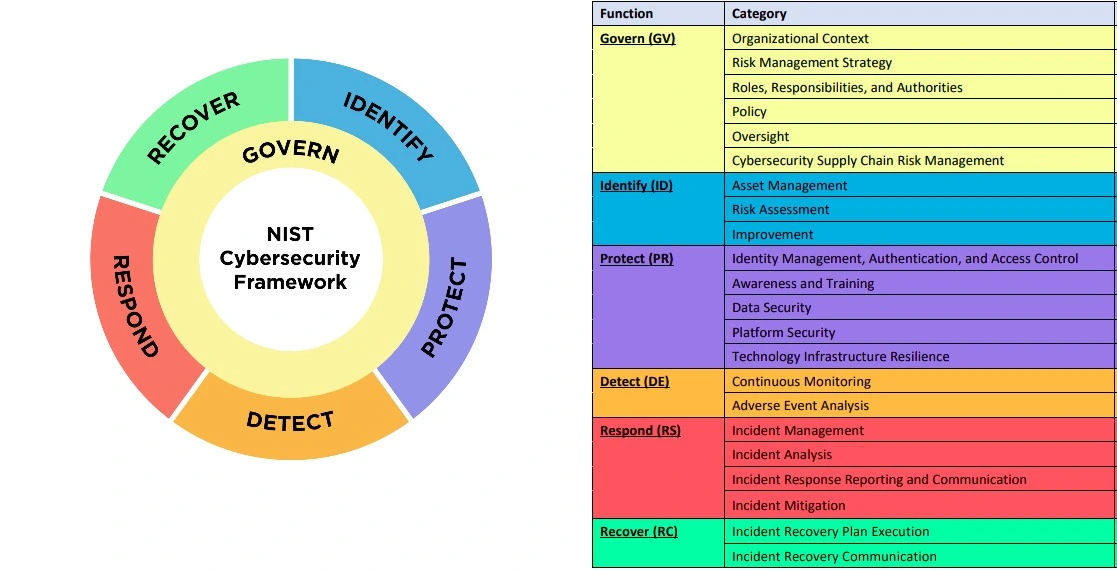
The images shows the newly added ‘Govern’ function.
Primary components of CSF 2.0
There are three primary components of CSF 2.0:
- Core: It refers to a set of cybersecurity activities and references that provide a high-level, strategic view of an organization’s cybersecurity posture. The core is organized into six functions. Govern, Identify, Protect, Detect, Respond, and Recover, which are further divided into 22 categories and 106 subcategories.
- Tiers: Organizations can identify their current state of cybersecurity with the help of tiers. There are 4 tiers: Partial, Risk-Informed, Repeated, and Adaptive.
- Profiles: Profiles are divided into “current” and “target” profiles.
We will cover each component pf CSF 2.0 in detail.
Core functions of CSF 2.0
There are six core functions within NIST CSF 2.0.
-
Govern: This function involves cybersecurity risk management strategy, expectations, and policies.
Category Key points Security Enhancements Organizational Context Involves recognizing the unique aspects of the organization, its mission, goals, operational environment, regulatory requirements, and risk appetite, that influence how it manages cybersecurity risks
It includes
understanding Business Needs and Drivers
- Tailoring the Framework
- Risk Management
- Resource Allocation
- Communication
- Continuous Improvement
- Mission and Objectives
- Stakeholder Expectations
- Legal, Regulatory, and Contractual Requirements
- Threat LandscapeStrategic Alignment
Asset Protection
Clear Direction
Accountability and ResponsibilityRisk Management Strategy Risk management processes are established, managed, and agreed to by organizational stakeholders.
Understanding and articulating risk tolerance is essential for making informed decisions about which risks to mitigate, accept, transfer, or avoid. It includes
- Identifying Risks
- Assessing Risks
- Developing Risk Treatment Plans
- Risk Acceptance
- Continuous MonitoringPrioritization
Informed Decision-Making
Proactive Risk Mitigation
AdaptabilityRoles, Responsibilities, and Authorities Ensure clear accountability, define actions, and empower stakeholders for effective cybersecurity management.
Establishment and Communication
Leadership Accountability
Clear Assignment
Use of RACI Matrix
Comprehensive Coverage
Alignment with Organizational Structure
Regular Review and Update
Board and Executive Involvement
Cross-functional Collaboration
Empowerment and AuthorityClear Accountability
Effective Decision-Making
Improved Communication and Coordination
Reduced Risk of Human ErrorPolicy Policies establish guidelines and standards to ensure consistent cybersecurity practices across the organization. The below process is part of the policy lifecycle.
Policy Development and Implementation
Communication of Policies
Policy Enforcement
Regular Review and Update
Alignment with Organizational Context
Integration with Enterprise Risk Management
Supply Chain Considerations
Compliance and Regulatory Alignment
Documentation and AccessibilityClear Expectations
Consistent Practices
Risk Management
AccountabilityOversight Keeping a close eye on all aspects of cybersecurity
Continuous Monitoring and Evaluation
Performance Measurement
Feedback and Improvement
Governance Integration
Stakeholder CommunicationMaintaining Effectiveness
Promoting Accountability
Driving Continuous Improvement
Demonstrating CommitmentCybersecurity Supply Chain Risk Management Program and Strategy
Identifying and Assessing Suppliers and Third-Party Partners
Understanding Supply Chain Dependencies
Risk Management Integration
Supplier Prioritization
Contractual Security Requirements
Due Diligence
Continuous Monitoring
Incident Planning and Response
Post-Relationship Risk Management
Managing Supply Chain Risks
Communicating and Collaborating with SuppliersReduces Risk Exposure
Protects Critical Assets
Strengthens Resilience
Fosters Trust -
Identify: This function involves identifying assets, vulnerabilities, and threats within an organization’s environment.
Category Key points Security Enhancements Asset Management The company inventories all software components and data used in its service. This includes identifying which data is sensitive and requires additional protection measures.
- Asset Identification
- Asset Classification
- Asset Ownership and Responsibility
- Asset Inventory Maintenance
- Data Flow MappingTargeted Protection
Risk Prioritization
Improved Incident Response
Compliance
Efficient Resource ManagementRisk Assessment Conduct regular risk assessments to identify cybersecurity threats specific to the SaaS model, such as data breaches or unauthorized access to customer data.
- Risk Identification
- Risk Analysis
- Risk Prioritization
- Risk Communication
- Continuous Risk MonitoringInformed Decision-Making
Proactive Risk Mitigation
Efficient Resource Allocation
Improved Communication
AdaptabilityImprovement Continuous improvement is required to streamline the security tasks
- Iterative Assessments
- Feedback Loops
- Adaptability -
Protect: The Protect function focuses on securing assets and limiting the impact of a potential cybersecurity event.
Category Key points Security Enhancements Identity Management, Authentication, and Access Control Identity Management
- User Provisioning
- Role-Based Access Control (RBAC)
- Lifecycle Management
Authentication
- Multi-Factor Authentication (MFA)
- Single Sign-On (SSO)
Access Control
- Access Control Lists (ACLs)
- Policy EnforcementPrevents Unauthorized Access
Limits Damage from Breaches
Enforces Accountability
Facilitates ComplianceAwareness and Training Security Awareness Programs
Security Training
Phishing Simulations
Role-Based Training
Continuous LearningReduces Human Error
Empowers Employees
Strengthens Security Culture
Supports ComplianceData Security Encrypt sensitive customer data both in transit and at rest. Ensure that encryption keys are securely managed
Data Classification
Data Encryption
Access Controls
Data Masking and Tokenization
Data Backup and Recovery
Data Retention and Disposal
Data Loss Prevention (DLP)Confidentiality
Integrity
Availability
CompliancePlatform Security Secure Configuration
Vulnerability Management
Malware Defenses
Secure Coding Practices
Data Protection at Rest and in TransitReduced Attack Surface
Timely Vulnerability Management
Proactive Malware Defense
Secure Software Development
Data ProtectionTechnology Infrastructure Resilience Data Backup
Recovery Planning
Redundancy
Resilient Design
Physical ProtectionMinimizes Downtime
Protects Data
Ensures Business Continuity -
Detect: The Detect function monitors and detects cybersecurity events.
Category Key points Security Enhancements Continuous Monitoring Real-Time Monitoring
Alerting and Notifications
Security Information and Event Management (SIEM)
Anomaly Detection
Vulnerability Scanning
Threat Intelligence
Change DetectionEarly Threat Detection
Improved Incident Response
Enhanced Situational Awareness
ComplianceAdverse Event Analysis Event Correlation
Impact and Scope Assessment
Root Cause Analysis
Incident Declaration
Threat Intelligence Integration
Information SharingAccurate Incident Identification
Targeted Response
Proactive Risk Mitigation
Improved Situational Awareness
Collaboration and Information Sharing -
Respond: The Respond function involves responding to detected cybersecurity events.
Category Key points Security Enhancements Incident Management Incident Response Plan
Incident Triage and Analysis
Containment and Eradication
Recovery
Lessons Learned
CommunicationMinimizes Impact
Facilitates Recovery
Improves Security Posture
Maintains Stakeholder ConfidenceIncident Analysis Comprehensive Investigation
Root Cause Identification
Impact Assessment
Evidence Preservation
Threat Actor Profiling
Communication and CollaborationEffective Containment and Eradication
Informed Decision-Making
Improved Security Posture
Proactive Threat Detection
Legal and Compliance SupportIncident Response Reporting and Communication Internal Reporting
External Reporting
Stakeholder Communication
Public Communication
Lessons Learned
Post-Incident ActivitiesFacilitates Timely Response
Minimizes Damage
Enhances Collaboration
Supports Compliance
Promotes Continuous ImprovementIncident Mitigation Containment Strategies
Eradication
Activity Monitoring
Protective Technology
Coordination and CommunicationLimits Impact
Enables Faster Recovery
Improves Security Posture
Demonstrates Preparedness -
Recover: The Recovery function involves restoring systems and assets affected by a cybersecurity event.
Category Key points Security Enhancements Incident Recovery Plan Execution Plan Activation
Resource Coordination
Prioritization
System Restoration
Testing and Validation
Communication
Plan Review and ImprovementMinimizes Downtime
Ensures Business Continuity
Protects Data
Facilitates Continuous ImprovementIncident Recovery Communication Internal Communication
External Communication
Stakeholder Updates
Lessons LearnedFacilitates Coordinated Response
Minimizes Disruption
Maintains Trust and Confidence
Supports Continuous Improvement
Implementation Tiers of CSF
The NIST CSF implementation tiers are designed to help organizations understand the maturity of their cybersecurity risk management programs. The tiers range from 1 to 4, with each tier representing a different level of cybersecurity maturity:
- Tier 1: Partial: The organization uses informal procedures and knows very little about cybersecurity procedures and threats, with minimal internal cybersecurity coordination.
- Tier 2: Risk Informed: The organization has established policies and defined risk management procedures that are known to the entire organization. Procedures are reviewed frequently to match the needs of the business.
- Tier 3: Repeatable: Same as Risk informed but with established procedures and consistent review and update
- Tier 4: Adaptive: The organization prioritizes dynamically responding to changing risks and threats and continuously improving its cybersecurity procedures based on lessons learned.
Profiles of NIST CSF
The third primary component of NIST CSF is profiles. We create current and target profiles. The profile can be of the whole organization, any product, or any business unit where we want to improve the security posture. To create a profile, we need to understand the business requirements, sync with various teams, perform gap analysis, and create a detailed plan on how to fix the gaps identified and reach the target profile. There are multiple milestones to reach the target stage.
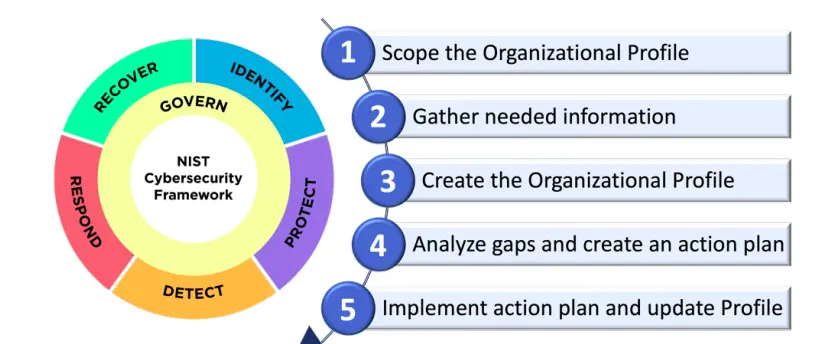
Best practices for maintaining NIST CSF Compliance in the cloud
-
Know your cloud service provider’s security measures: The first step towards maintaining NIST CSF compliance in the cloud is understanding your cloud service provider’s security measures and the service alignment with the NIST CSF framework. All major cloud service providers have stringent security controls in place, but it is important to familiarize yourself with them and ensure they align with the NIST CSF framework.
-
Use encryption for data protection: Encryption is a key component of data protection and a crucial aspect of NIST CSF compliance. Make sure all sensitive data stored or transmitted on your cloud infrastructure is encrypted using approved algorithms. This includes data at rest as well as data in transit.
-
Implement access controls: Controlling access to resources within your cloud environment is vital for maintaining NIST CSF compliance. Utilize Identity and Access Management (IAM) tools provided by your cloud service provider to manage user permissions and privileges effectively.
-
Regularly monitor your cloud environment: Monitoring your cloud infrastructure regularly helps detect any potential vulnerabilities or suspicious activities that could compromise your organization’s security posture. Set up alerts to track any unusual activity or changes made within your environment.
-
Conduct regular risk assessments: Conducting regular risk assessments allows you to identify potential risks within your environment and take steps to mitigate them before they turn into serious threats. This practice also aligns with one of the core functions of the NIST CSF - Identity.
-
Implement multi-factor authentication (MFA): MFA adds an extra layer of security to user authentication by requiring additional verification methods, such as a one-time password or biometric scan. This helps prevent unauthorized access and is recommended by the NIST CSF framework.
-
Keep your cloud infrastructure up-to-date: Regularly updating your cloud infrastructure and applications is crucial for maintaining NIST CSF-2.0 compliance. By doing this, the likelihood of a cyberattack is decreased by ensuring that any known vulnerabilities are patched.
Following these best practices will help organizations maintain NIST CSF compliance in their cloud environment and ensure the security of their critical assets and information. It is also important to note that maintaining compliance is an ongoing process, and regular audits should be conducted to identify any gaps or areas for improvement. By staying vigilant and following these practices, businesses can strengthen their security posture and protect themselves from potential cyber threats in the cloud.
Various public cloud services aligned with NIST CSF 2.0
When using the public cloud, there are multiple native services available that can help us align with the NIST CSF and improve the overall security posture. The table below maps the cloud services with the primary functions of NIST primary functions. Below is a list of various native services supported by various cloud providers at the time we were writing the blog.
| CSF Function | AWS | GCP | Azure |
|---|---|---|---|
| Govern | AWS Identity and Access Management (IAM) AWS Organizations AWS CloudTrail AWS Config AWS Artifact AWS Compliance Center | Security Command Center Policy Intelligence Cloud deployment manager Supply chain (GKE Security posture) Policy Compliance(GKE Security posture) | Azure Policy Azure Blueprints Azure Compliance Manager Azure Security Center Azure Monitor Azure Governance Visualizer (AzGovViz) Microsoft Compliance Score |
| Identify | AWS Config AWS CloudTrail Amazon Inspector AWS Risk and Compliance Program: AWS Cloud Adoption Framework (CAF) | Cloud identity and access management Cloud asset inventory Security command center GKE security posture | Azure Security Center Azure Active Directory (Azure AD) Azure Policy Azure Blueprints Azure Advisor |
| Protect | AWS Identity and Access Management (IAM) Amazon Virtual Private Cloud (VPC) AWS Key Management Service (KMS) AWS Shield AWS WAF Amazon GuardDuty AWS Certificate Manager AWS CloudTrail AWS Config | Cloud identity and access management Vpc service controls Shielded VM’s Security Command Center Policy Intelligence Cloud deployment manager Access approval API | Azure Active Directory (Azure AD) Azure Information Protection Azure Security Center Azure Firewall Azure Key Vault Azure Multi-Factor Authentication (MFA) Azure Virtual Network |
| Detect | Amazon GuardDuty AWS CloudTrail Amazon Macie AWS Network Firewall Amazon CloudWatch AWS Config | Security Command Center Event threat detection Cloud logging and cloud monitoring GKE Security posture | Azure Security Center Azure Sentinel Azure Monitor Microsoft Defender for Cloud (formerly Azure Security Center) |
| Respond | AWS Lambda Amazon Simple Notification Service (SNS) AWS CloudWatch AWS Step Functions AWS Security Hub Amazon Detective | Security Command Center Event threat detection Cloud functions and pub/sub Cloud logging and cloud monitoring | Azure Security Center Azure Sentinel Azure Monitor Microsoft Defender for Endpoint Azure Logic Apps |
| Recover | AWS Backup Amazon S3 Glacier AWS CloudFormation Amazon Route 53 AWS Elastic Beanstalk AWS CloudEndure Disaster Recovery | Google cloud storage Persistent disk storage Cloud SQL backups Cloud KMS Google Kubernetes Engine(GKE) backups Disaster recovery planning guide | Azure Backup Azure Site Recovery Azure Storage |
Final words
NIST CSF-2.0 is an impressive framework that covers all aspects of cybersecurity, its redesigned structure now involves and focuses on topics that were taken lightly in the past by organizations like open source compliance management. It is the cherry on top of current best practices which can guide organizations to streamline their cybersecurity posture.
I hope you found this blog post informative and engaging. I’d love to hear your thoughts on this post. Let’s connect and start a conversation on LinkedIn. Looking for help with securing your infrastructure or want to outsource DevSecOps to the experts? Learn why so many startups & enterprises consider us as one of the best DevSecOps consulting & services companies.
References
Stay updated with latest in AI and Cloud Native tech
We hate 😖 spam as much as you do! You're in a safe company.
Only delivering solid AI & cloud native content.